This article is providing instructions on how to public a server/device to the internet using http. This article will go through the basic configuration.
After logging into to the Fortinet portal, got to Firewall Objects –> Virtual IP –> Virtual IP, select Create New

There are number of parameters:
Name: Short description of services e.g. DVR HTTP-80
External Interface: this is the port connected to the internet link with the public IP address.
External IP Address/Range: this use only need if you have more that one IP address configured on the port. If not, you can leave the default 0.0.0.0
Mapped IP Address/Range: Enter the internal server IP address of device. e.g. our DVR 192.168.0.12
Port Forwarding: tick this option if you are using custom ports from the default e.g. external service port is 5000 from the outside connecting to (map to) port 80 on the internal server.

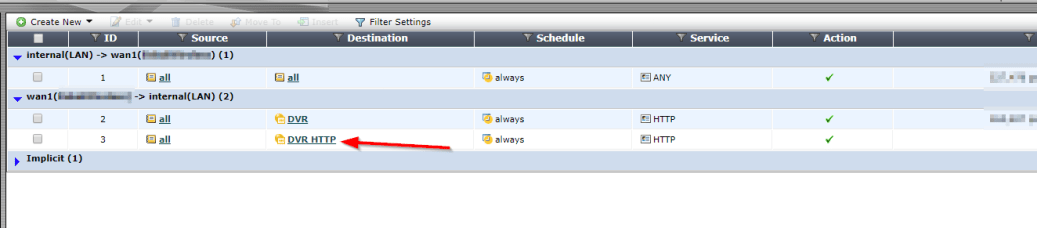
Go to Policy –>Policy –> Create New

Select the Source Interface/Zone to external port.
Select destination Address to the Virtual IP created earlier and select Service to HTTP since we are using port 80. If the service is not list add it with the custom ports. Select Enable NAT to allow external IP address to access the internal device through the fortinet.

Once save by clicking ok, it will be listed under the external port source port column in the Policy section.