This article is about setting a public accessible Web App Service which allowing it to connect privately to a Azure VM within a Virtual network (VNET).
I was given a task to assist our developer to connect a Web App with customized code to interface with a Azure VM hosting an SQL server database and customized web services. The design requirements were as followings:
- The Web App must be accessible public with no restrictions
- The Azure VM must be accessible by the Web App Service only
- The services must use most cost effective Azure resources to accomplish this result.

After reviewing the requirements and accessing what Azure features are available to accomplish the task. The following solution was provided.
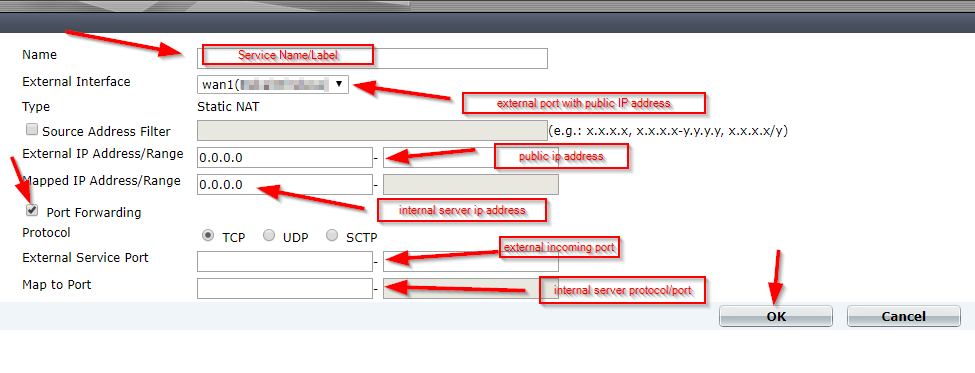
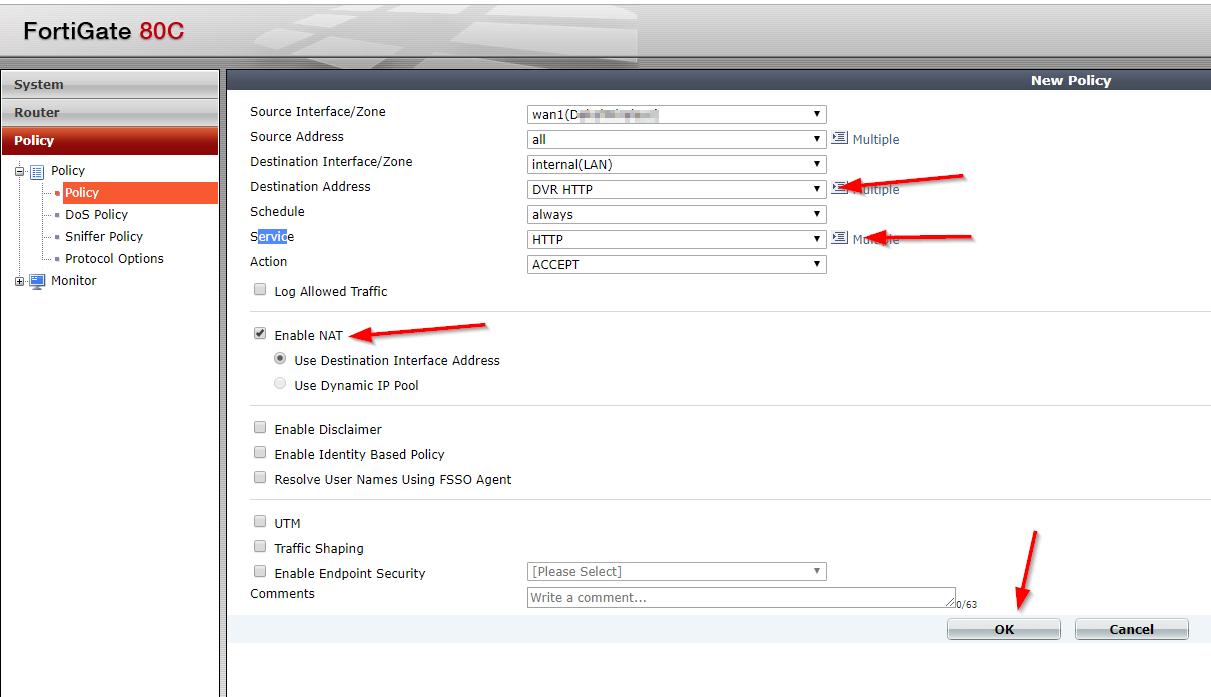
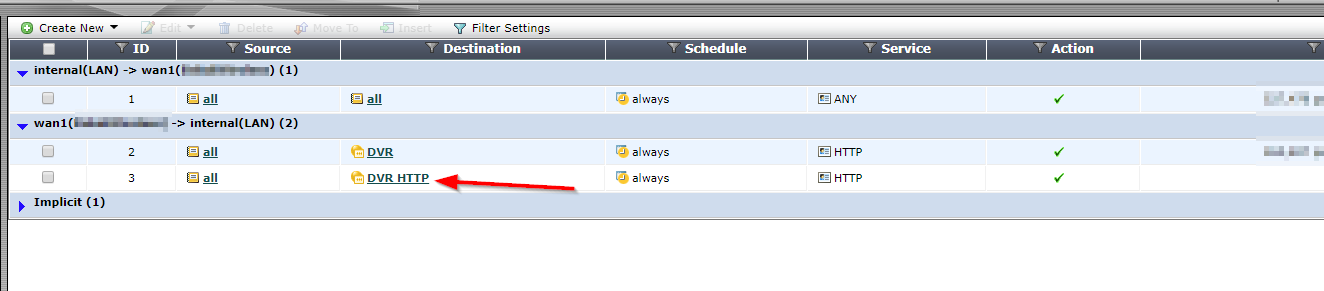
- The Web App Service must have the supported pricing tier of at least Basic or Standard to use it with VNet.
- Configure a Subnet with CIDR notation of /26 which will facilitate the private connection from the Web App.
- Configure the VNET Integration to connect the Web App to the subnet created previously for the private communication.
- Network Security Group (NSG) can be used to limit who can accept connections from the Web App service in the private subnet.
Microsoft Documentation reference:
https://learn.microsoft.com/en-us/azure/app-service/configure-vnet-integration-enable